via zerohedge:
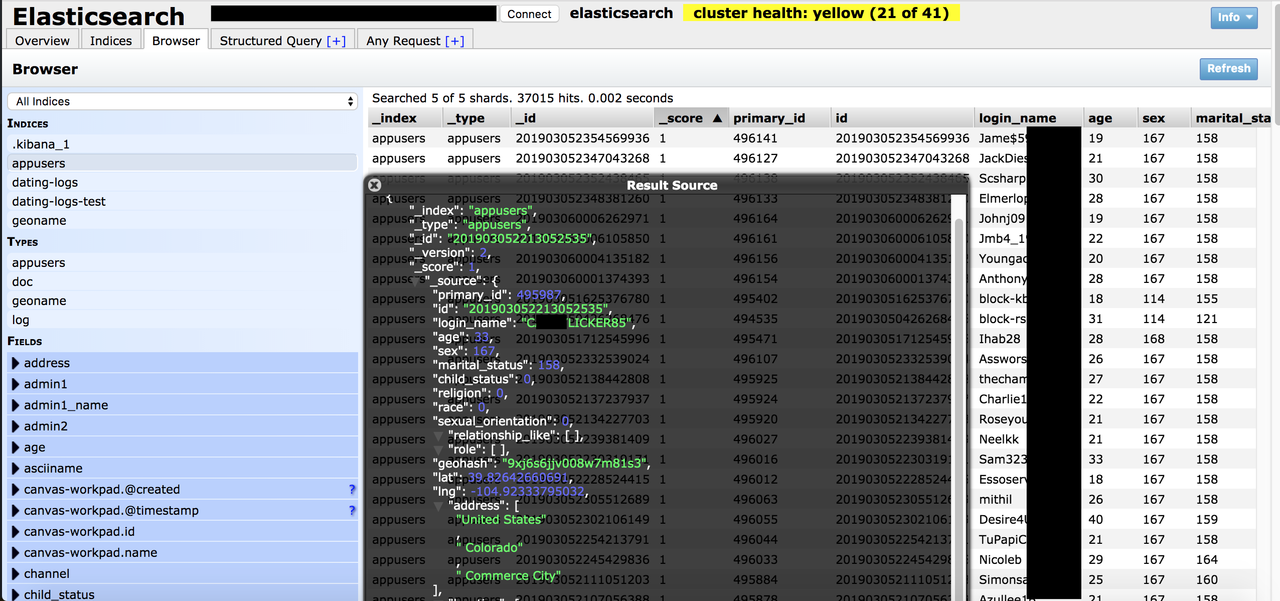
On May 25th, security researcher Jeremiah Fowler discovered an unsecured Elastic database associated with an entity in China had exposed 42.5 million records of mostly American dating app users.
Fowler noticed an I.P. address, located on a U.S. server with many of the users based in North America. He examined the sever even closer and found Chinese text inside the database that read: 模型更新完成事件已触发,同步用户到 (Google Translate: The model update completion event has been triggered, syncing to the user.)
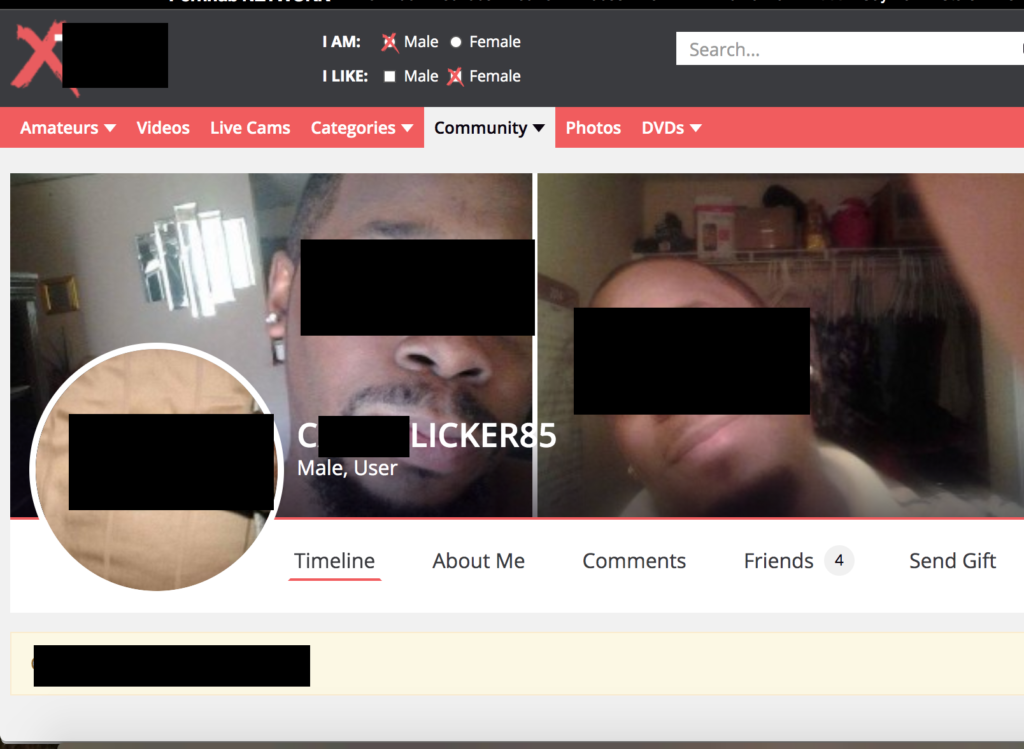
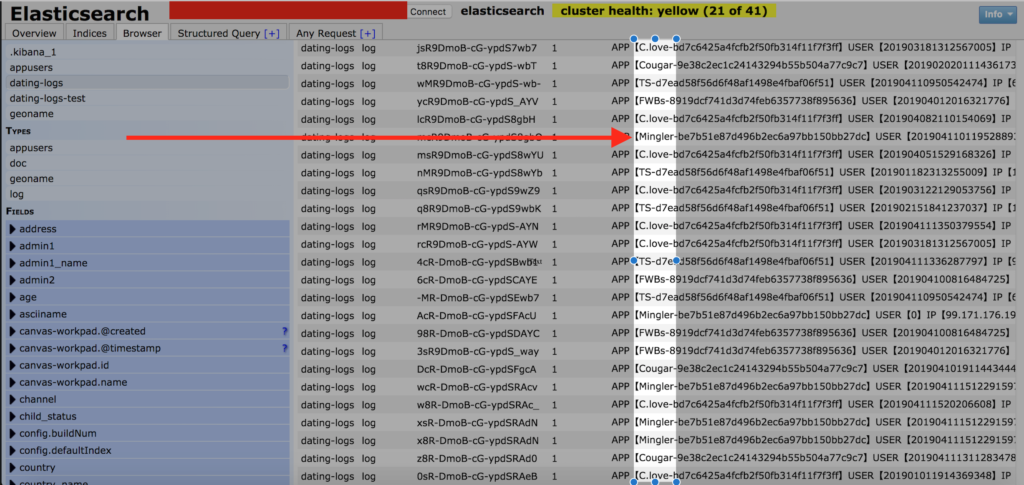
“The strange thing about this discovery was that there were multiple dating applications all storing data inside this database,” Fowler wrote in a blog post on Security Discovery. “Upon further investigation, I was able to identify dating apps available online with the same names as those in the database.”
He said, “that despite all of them using the same database, they claim to be developed by separate companies or individuals that do not seem to match up with each other. The Whois registration for one of the sites uses what appears to be a fake address and phone number. Several of the other sites are registered private and the only way to contact them is through the app (once it is installed on your device).”
Fowler was able to find users’ real identity in a matter of minutes: “The dating applications logged and stored the user’s I.P. address, age, location, and user names,” he wrote. “Like most people, your online persona or user name is usually well crafted over time and serves as a unique cyber fingerprint.”
In an email to CyberScoop, Fowler said a sampling of 10,000 users revealed that 8,063 were Americans, 356 were from the U.K., 219 from Canada and 151 from Australia.
Approximately 42.5 million records were exposed, Fowler said. He wasn’t sure who controls the database nor its exact location. But the site’s Whois domain registration was located on a subway line in Lanzhou, China.
Dating apps mentioned in the database include a diverse range to collect as much data as possible:
- Cougardating (Dating app for meeting cougars and spirited young men: according to the site)
- Christiansfinder (an app for Christian singles to find ideal match online)
- Mingler (interracial dating app)
- Fwbs (Friends with benefits)
- “T.S.” I can only speculate it is an app called “T.S.” that is a Transsexual Dating App
“I am not saying or implying that these applications or the developers behind them have any nefarious intent or functions, but any developer that goes to such great lengths to hide their identity or contact details raises my suspicions,” Fowler wrote. “Call me old fashioned, but I remain skeptical of apps that are registered from a metro station in China or anywhere else.”
Commenting on the compromised database, Nabil Hannan, managing principal, financial services, at Synopsis, told S.C. Media:
“In this particular case, there’s a lot of personal and private information that users trust dating sites with.
Although the data that was leaked did not include anything sensitive, per se, it does have usernames (from which a person’s full name can often be inferred) along with age and location information” and “may be enough to allow attackers to cause some level of damage depending on the type of information publicly available about the people whose data have been leaked.”
Fowler’s findings could be another example of Chinese hackers attempting to extract personal data from Americans.