In the phishing campaign spotted by researchers at phishing simulation and security awareness training outfit KnowBe4, the attackers promise to provide a list of active infections in the surrounding area to trick their potential victims into clicking a link embedded in the message and leading to a credential phishing page.
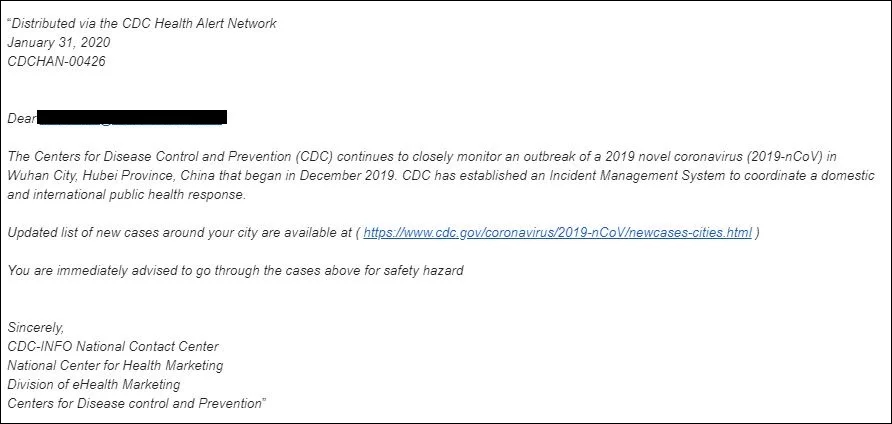
In a sample phishing email spotted by KnowBe4, the attackers try to pass their spam as an official alert message distributed via the CDC Health Alert Network.
The targets are then informed that the “CDC has established an Incident Management System to coordinate a domestic and international public health response.”
The phishers then throw in their lure, in the form of a link promising to provide the recipient with an updated list of new cases of infection around their city.
“You are immediately advised to go through the cases above for safety hazard,” the attackers add, trying to induce a sense of urgency that would trick the target into acting on instinct and not think about the potential dangers ahead.
The link is camouflaged as a link to the official CDC website and it is used to redirect the victims to an attacker-controlled and Outlook-themed phishing landing page used for collecting and stealing user credentials.
KnowBe4 CEO Stu Sjouwerman told Bleepingcomputer that these emails were spotted on Friday afternoon. “We expect a variety of campaigns with different payloads to arrive shortly, Emotet has already been seen using this same social engineering tactic in Japan, leveraging the Coronavirus.”
“This phish leverages public fear over a widely publicized virus threat,” Eric Howes, principal researcher at KnowBe4 also told us.
“It is a bit unusual in that the bad guys are usually not so nimble in exploiting current events (they seem to put more time/effort in developing payloads and methods for obfuscating payloads). Then again, this story has been building for several weeks.
The phishing email itself is rather well done, so I’m guessing whoever is behind it modeled the email after existing CDC press releases.
There is a subject/verb agreement error in the second paragraph, but it’s a common one that plenty of folks make. Still, not the kind of error one would expect from a professional PR operation, which the CDC undoubtedly has. Doubtful whether most readers would notice, though.”
https://www.pcmag.com/news/new-coronavirus-strain-nope-just-hackers-trying-to-spread-malware